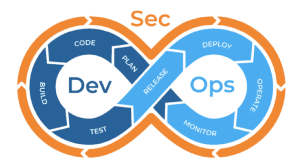
Introduction
Here at Collabify, we aim to automate most things we can and to give quick feedback to our client teams. I have personally seen what a major difference a shift-left approach can bring to organizations implementing security standards in continuous integration and continuous delivery (CI/CD) practices. In this article, I will explain what shift left means in the context of security, why it is important, and how to implement it in your organization's CI/CD pipeline.
The term "shift left" refers to the practice of integrating security into the software development process as early as possible, rather than waiting until the end of the development cycle or in some cases waiting as much as a few months into product development. This approach allows organizations to identify and address security vulnerabilities and risks at the earliest stage possible, making it easier to prevent them from becoming major issues. By shifting security left, organizations can also ensure that security is integrated into the development process, rather than being treated as an afterthought.
Reasons
There are several reasons why shift-left is becoming increasingly important in today's digital landscape. One of the main reasons is the increasing number of cyber threats and attacks that organizations are facing. The complexity and frequency of releases have massively increased over the past few years due to the demand for new features as well making it difficult for "manual" security scans to keep up with it. By shifting security left, organizations can better protect themselves from these threats by identifying and addressing vulnerabilities early on. Additionally, shift left can help organizations comply with regulations and industry standards, such as PCI-DSS and HIPAA, which require organizations to implement security measures throughout the software development process.
To implement
To implement security in your organization's CI/CD pipeline there are a few key steps you can take. First of all - and this is true not only for security - let the teams self-organise. Giving responsibility to your delivery teams will encourage them to increase efficiency, and quality and work as a unit. It is also important that you establish a security-conscious culture within your organization. This means creating a culture where security is everyone's responsibility and where all team members are aware of the importance and potential implications.
It is also very important to start from a good base. By implementing SAST (static application security testing you can filter out any vulnerabilities that you might have introduced by using external libraries. SAST concentrates on scanning your source code and associated dependencies. If you're using Jenkins OWASP Dependency Check can be a great solution.
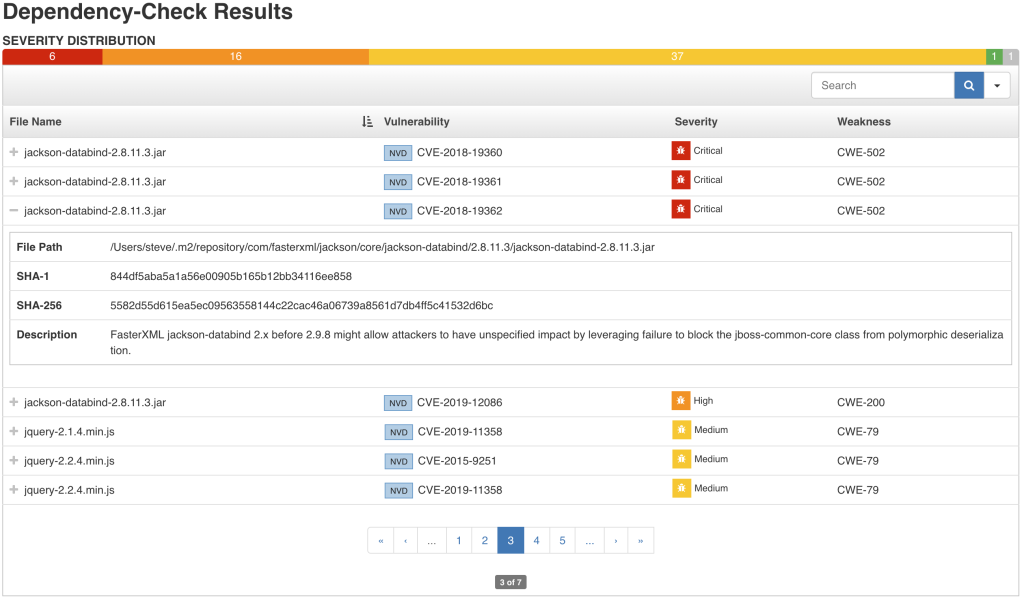
Enhancements
You can further enhance security by implementing DAST which will concentrate on a deployed application and scenario-based non-functional testing, however technically speaking that's not part of the "shift-left" methodology.
Another enhancement things by implementing security scanning in earlier stages such as pre-commit. This will help to ensure that security testing is done regularly and that vulnerabilities are identified and addressed early on.
Conclusion
In conclusion, shift left is an approach to security that is becoming increasingly important for organizations implementing CI/CD practices. By shifting security left, organizations can better protect themselves from cyber threats, comply with regulations and industry standards, and improve the overall security of their software development process. To help implement security in your organisation please be sure to reach out to us at info@collabify.net